My Tor Relay: If you build it, they will come
A showcase of how easy it is to setup and operate a Tor Relay. Everybody should support the right to privacy on the Internet and this is a very easy and convenient way to do it if you already have a VPS running somewhere.
Some background
I assume that all of you know the Tor project and what it does. My first experience with it, many years ago, effectively demonstrated the cost of anonymity and routing traffic through multiple nodes. It was painfully slow. Down to the point where I really understood that only people doing bad stuff would have the patience to wait for their scummy pages to load. I did not have the patience so I stopped using Tor altogether.
Recently I stumbled across this fine article about operating a Tor relay and decided to see if Tor was still as slow as it used to be. It was an entirely different experience. It was fast, pages would load with ease and the idea of replacing your browser with the Tor browser was not far fetched at all.
The very simple explanation behind this change is that the bandwidth available have increased drastically. This can be seen from this graph generated using Tor metrics.
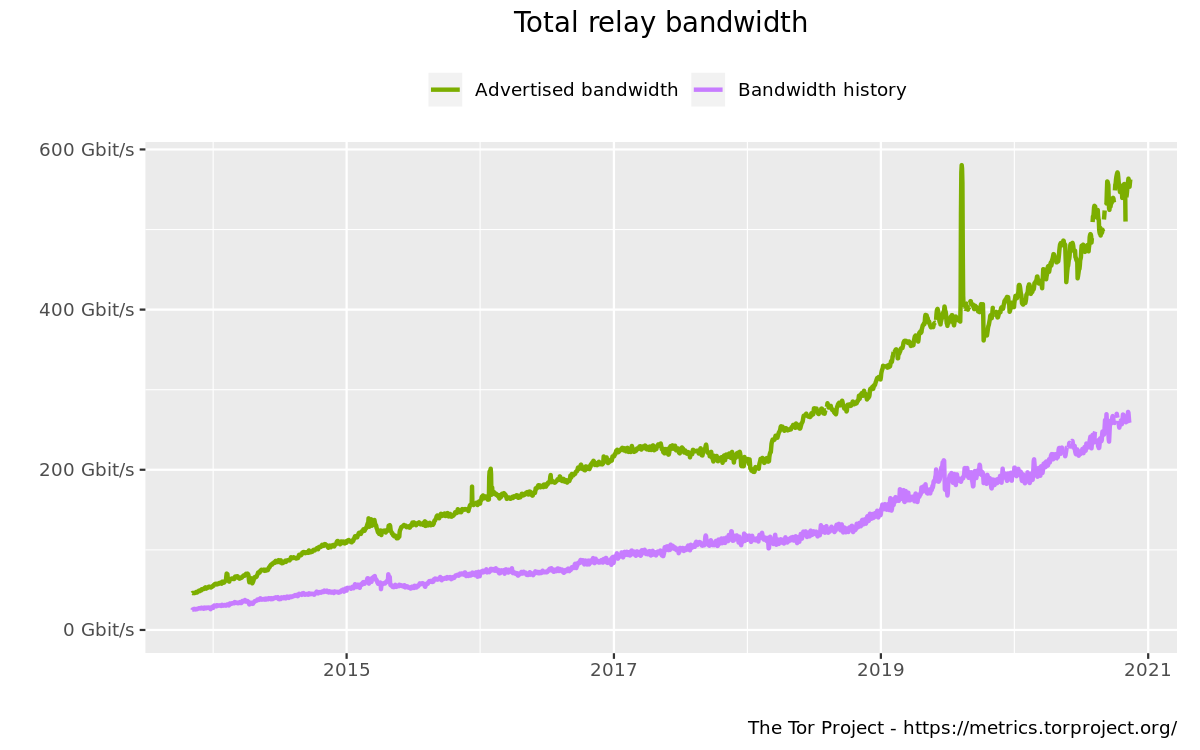
I was intrigued by both the significantly improved user experience and how apparently easy it is to operate a Tor Relay according to the aforementioned article. I wanted to dip my toes and try to host a Tor Relay as well!
Relay??
Most connections in the Tor network are built using a chain of three relay servers. These relay servers are of three different kinds:
- Guard relay
- Middle relay
- Exit relay
The first in the chain is called the Guard server. This server will know your IP/identity but will not know what you are trying to connect to. The next is called the Middle relay. This one redirects traffic from the Guard relay to the Exit relay oblivious to both your identity and your destination. The Exit relay connects you to your actual destination - be it legal or illegal content.
Exit relays require a great amount of conviction as the IP of your server will the one law enforcement finds if some of the traffic you relayed were for illegal purposes. You will have to explain over and over again that you are simply running an Exit relay and are not responsible for the traffic they are seeing. You probably also have to respond to quite a bit of subpoenas or other information requests explaining that you cannot provide them with any information due to the nature of Tor. The Tor project advises against using a home server as Exit relay to avoid getting raided by law enforcement. Operating Exit relays are for true believers and the operators should praised eternally for their conviction.
Middle and Guard relays however bears little to no risk of having to deal with law enforcement as you are simply relaying a connection from one Tor node to another. I do not have enough conviction and fortitude to run an Exit node, so I wanted to run a simple Guard/Middle relay.
Relay phases
Each new relay on the Tor network goes through a set of phases to determine its bandwidth and stability. These phases are most adequately described in the article mentioned earlier and a Tor blog article about this. The most essential point is that every non-exit relay stats out as a Middle relay. If the relay is relatively stable the "middle probability" will increase. This is the probability that your relay is selected as the Middle relay when a circuit is being created. If bandwidth and stability is above average, the relay will be promoted to a Guard relay.
Choice of VPS
I did not have a VPS spinning at the time, so I had to find a hosting provider and spin one up. My thoughts went straight to DigitalOcean. However after reading some recommendations about hosting providers for Tor Relay it was clear that large hosting providers such as DigitalOcean/OVH/Hetzner should be avoided if possible for new relays.
The whole point of the Tor project is to distribute and decentralize such that anonymity can be achieved by "randomly" selecting 3 servers to route your traffic through. If the majority of the servers lie within the control of 1, 2 or 3 hosting provides you do not really have a decentralized system. Below is another cool graphic generated by Tor metrics detailing network bubbles of relays per their autonomous system
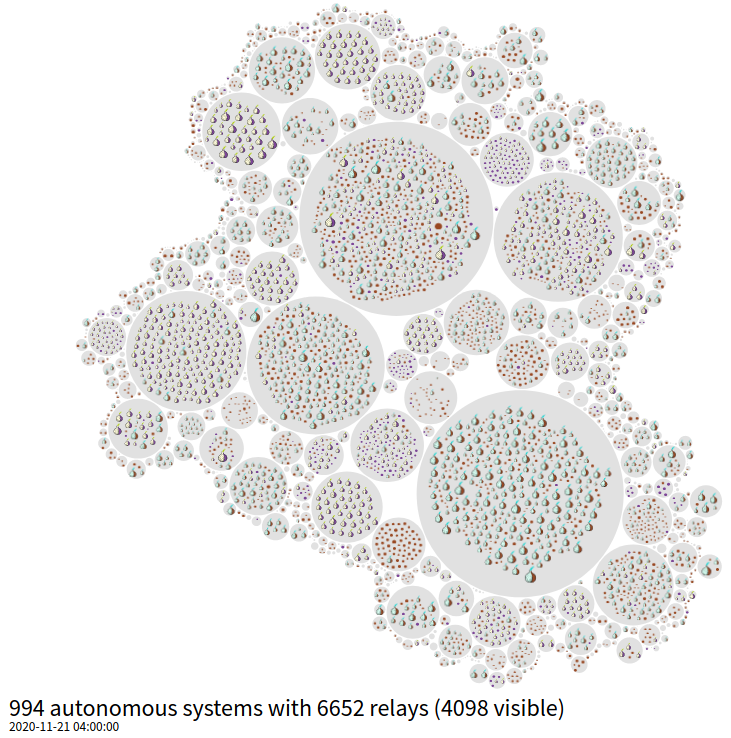
The two largest bubbles belong to Hetzner and OVH and they clearly "control" a large portion of the Tor network. I needed to find a not so popular hosting provider to help decentralize the Tor network.
I googled a bit around and found liteserver.nl which is a Dutch hosting provider providing affordable VPSs. For a multitude of reasons, described in my post about my digital garden, I picked the 5 EUR VPS plan HDD-1G. This provide you with 1 CPU core, 1 GB of RAM, 512 GB of HDD storage which is plenty for a Tor relay. The only downside is that we only get 6 TB of bandwidth and bandwidth is king in the world of relays. On top of that the bandwidth is the sum of ingoing and outgoing traffic. This means that I can only provide 3 TB of bandwidth to the network as a relay relays traffic - what comes in must go out again. This is probably one of the reasons that other relay operators select Hetzner or OVH due to bandwidth. The cheapest Hetzner VPS gets you 20 TB bandwidth for 2.89 EUR and for OVH unlimited bandwidth for 5.52 dollars. I still went with liteserver as I needed the 512 GB HDD storage for other projects. I picked Debian as the OS and onwards I went with my new VPS.
Installation
Installing the Tor relay on Debian-based systems is very easy. You add the Tor package repository, apt-get update && apt-get install tor and then you just need to create a configuration file in /etc/tor/torrc.
Configuration
My configuration is as follows:
# General config IPv4 + IPv6
Nickname DebatableMink
ORPort 9001
ORPort [2a04:52c0:101:5b7::468c]:9001
ExitRelay 0
SocksPort 0
ControlSocket 0
ControlPort 9051
CookieAuthentication 1
AccountingMax 180 GBytes
AccountingStart day 23:50
AccountingRule sum
RelayBandwidthRate 4000 KBytes
RelayBandwidthBurst 8000 KBytes
I have named my relay DebatableMink (I always name stuff with a randomly selected combination of an adjective and an animal) and opened the relay to connections from both IPv4 and IPv6. These ports can be freely selected as they are simply broadcast to the Tor network. I disable exit relaying, the socks proxy port and the control socket, but enable a control port with cookie authentication. This is used by nyx which I will get back to. Last we have the most essential part of the configuration, the rate limiting. My choice of VPS gave me 6 TB of bandwidth where bandwidth is defined as the sum of incoming and outgoing traffic. The configuration rate limits in two different ways. First,
AccountingMax 180 GBytes
AccountingStart day 23:50
AccountingRule sum
states that from 23:50 to 23:50 the next day, Tor should not consume more than 180 GB of bandwidth looking at both incoming and outgoing traffic. If we reach 180 GB before 23:50, the relay is simply shut down until we reach 23:50 again. This allows my relay to be running every day of the month instead of burning through the bandwidth in a matter of days. The last two lines,
RelayBandwidthRate 4000 KBytes
RelayBandwidthBurst 8000 KBytes
specifies a cap on the relaying speed. On a good 1Gbps connection, 180 GB will not last an entire day if it is not rate limited. If I did not have this, my relay would reach 180 GB within the first couple of hours disabling it until the next day. Limiting the relaying speed allows my relay to be useful for almost the entire day while still providing adequate speeds. And that is it. Restarting the Tor service after changing the configuration and it is just minding its own business relaying traffic.
Monitoring
You can allow Tor to mind its own business, it is perfectly capable of doing so and will abide by the rules set in the configuration. However if you are ever-curious, you might want to see what is actually going on right now!
nyx is a fine little tool to do exactly this. You install it using apt and simply run the command nyx and then you will have a fine graphical display in your terminal showing exactly what is happening with your relay. It shows a graph of the current bandwidth, a list of connections, the configuration used and so on: 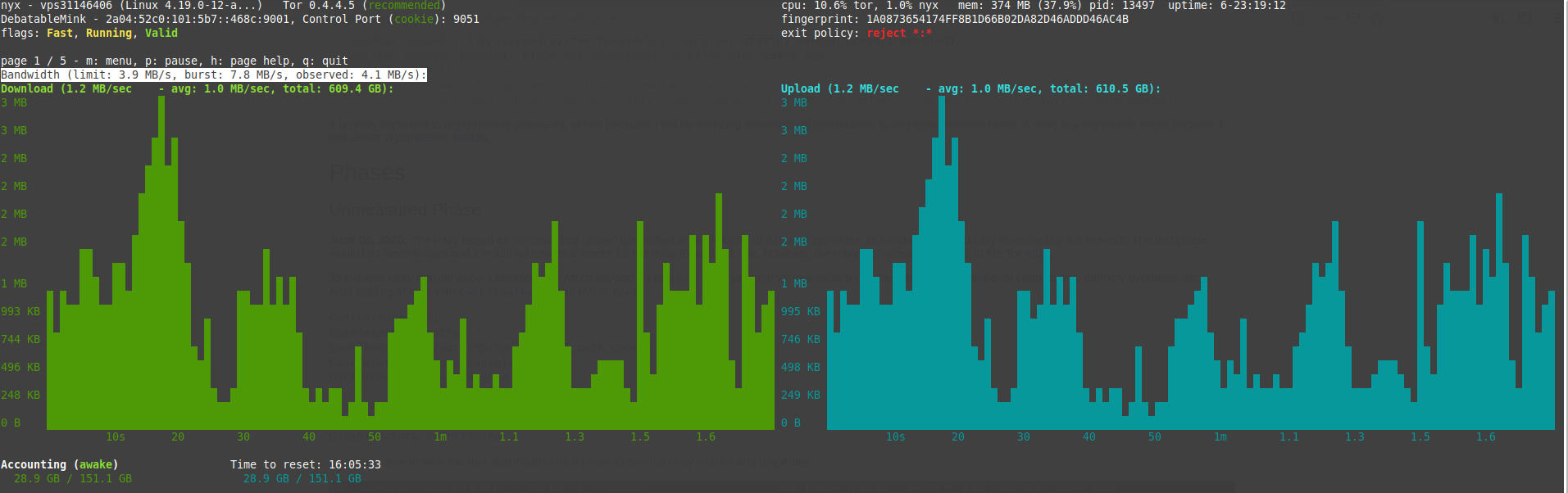 You can also go to the Tor metrics site and search up your relay:
You can also go to the Tor metrics site and search up your relay: 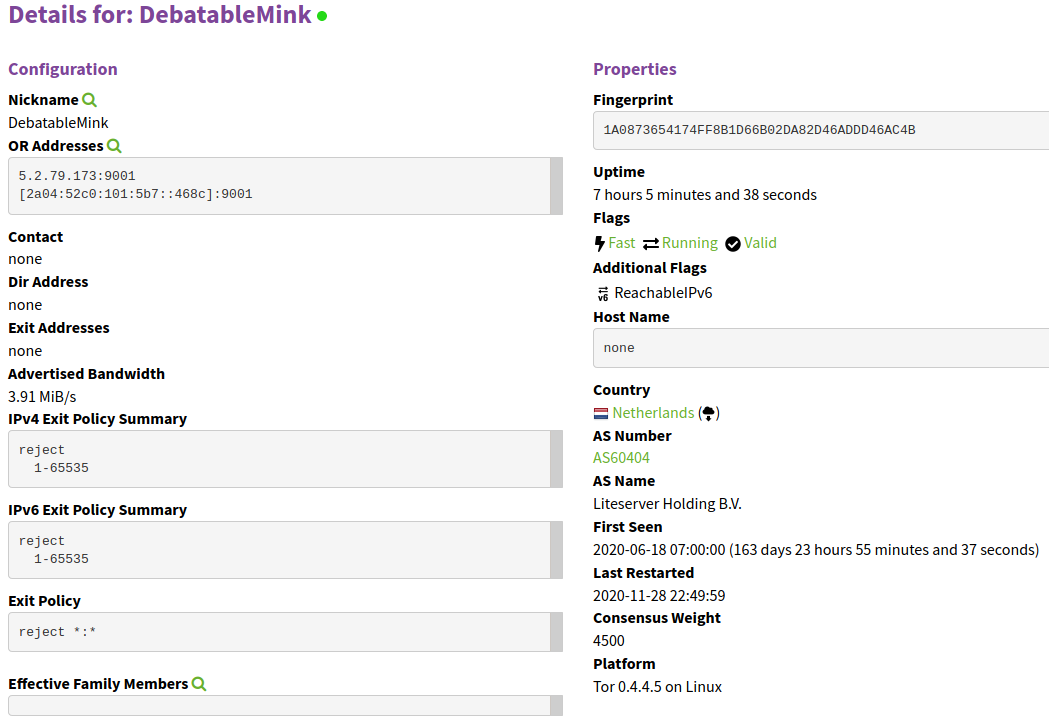
Why does it matter?
I care about free speech and privacy. I do not like the thought of potentially having every action on the Internet scrutinized by law enforcement, my own government or a foreign government. I do however have the freedom of both using Tor and not being prosecuted for setting up a Tor relay.
Imagine being an activist against your own totalitarian government. You actively required Tor or other means of keeping your privacy to not get prosecuted. You would wish that some of the more "free" global citizens would spend 5 EUR and a couple of minutes to setup a Tor relay.
It is very easy to setup your own Tor relay. The hardest part is probably to pick a good hosting provider for you and your needs. Please do support the Tor network as free speech and privacy also matters on the Internet.
Sidenote
If you are limited on bandwidth but still want to help you can run a Bridge. In anti-Tor countries all Tor nodes are IP banned such that their citizens cannot connect to the Tor network. A Bridge is essentially an unlisted Tor node which will allow censored users to actually get on the Tor network. As stated by the Tor project: "Bridges are relatively easy, low-risk and low bandwidth Tor nodes to operate, but they have a big impact on users. A bridge isn't likely to receive any abuse complaints, and since bridges are not listed in the public consensus, they are unlikely to be blocked by popular services.". The official guide for setting up a bridge can be found here